This report was done for course Tunkeutumistestaus ict4tn027-3007 organized by Tero Karvinen. The course information and assignment descriptions in finnish can be found at https://terokarvinen.com/2021/penetration-testing-course-2022-spring/.
a) Middle. Change a request with a man-in-the-middle proxy.
The environments used for this task were Kali Linux version 2022.01, Damn Vulnerable Web Application (DVWA) version 1.0.7 and Burp suite community edition 2021.10.3. Kali had the latest updates installed on 12.5.2022 at 18:00.
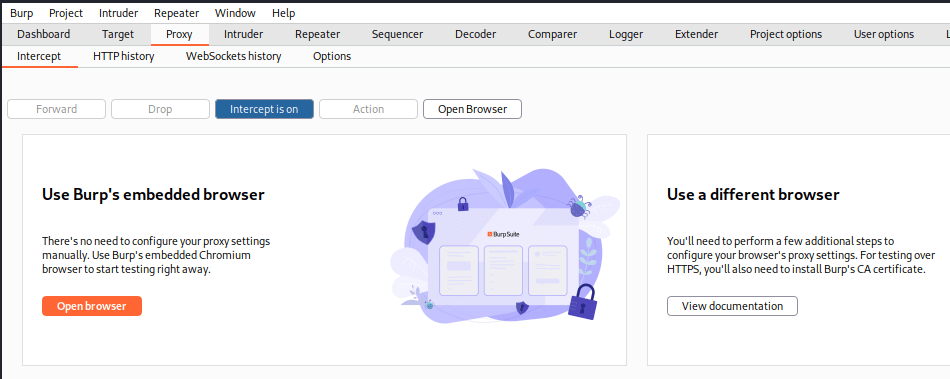
The Burpsuite interface is easy to navigate. A tab called proxy leads to the proxy tool. I opened the “Intercept” tab and clicked on the “Open browser” button. I made sure that intercept was on. A Chromium based browser opened with the proxy configuration already set. The proxy works also with other browsers, but then the proxy has to be manually set. The proxy settings can be seen under “Proxy” tab and selecting a sub-tab “options”.
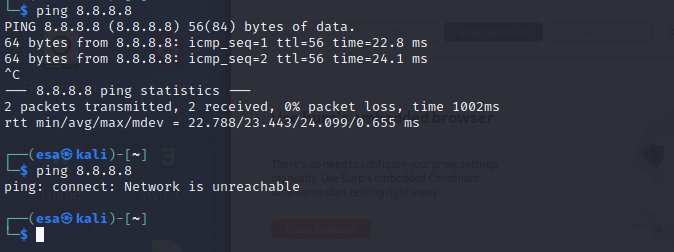
Next I disabled any internet adapters on the system to minimize the chances of accidentally scanning wrong targets or leaking packets to wrong sites. Pinging Google DNS server confirmed the internet connection was gone.
Next I started the Metasploitable 2 virtual machine that includes the DVWA. I used nmap in the virtual network to enumerate the correct host. Then I navigated to the site on my Kali and logged in with the default admin credentials.
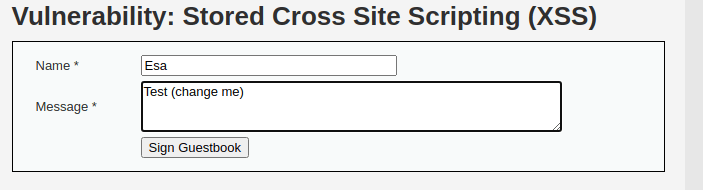
I used the “XSS stored” page to demonstrate the changed request. The original comment I wanted to insert was as is displayed below:
I clicked “Sign Guestbook” and intercepted the request in Burpsuite. The intercepted request looked like this:
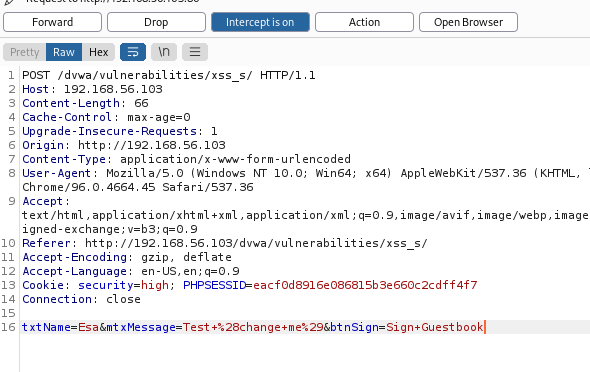
I changed the query string to contain other data than what was inserted in the original text box.
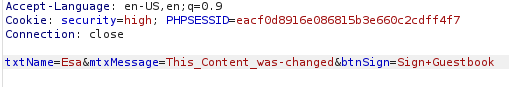
I forwarded and the request and checked what was inserted into the comments of the page.
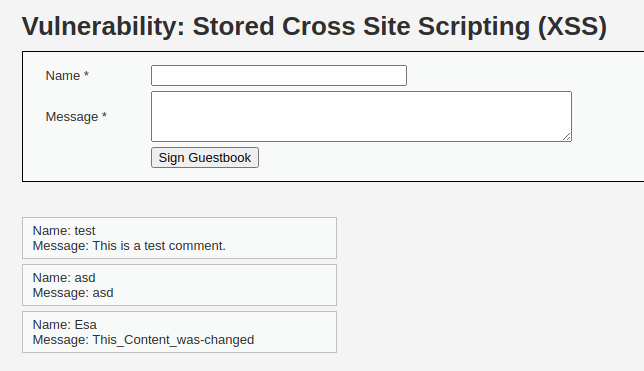
The bottom comment displays what was finally inserted into the database. The data was manipulated and a forged comment was inserted into the site, proving the request was altered.
b) Cheatsheet – collect the best tricks, commands and techniques from your and others reports. (just making notes is enough, no need to perfom tests)
Ghidra seems useful for software reverse engineering and analysis.I have never used this before, will check it out for sure later.
UDP scan might reveal some interesting services on some targets while using Nmap. Parameter used is -sU.
I have used gobuster a lot for website directory enumeration. Dirbuster supports also sub-directory enumeration. Possible switching to use application instead.
Nbtscan can be used to enumerate Netbios users. Will be useful for later use.
Legion could save some manual work? It is supposed to be semi-automated pen testing tool which combines bruteforce and automation. At least the default credentials are tested for every service.
d) All the assignments here. A direct link to each assignment’s submission.
Starting assignment:
H1:
H2:
H3:
H4:
H5:
H6:
f) Voluntary, Korkki: If you have broke into machines in Challenge.fi or HackTheBox, list them here. Seperate clearly non-retired machines from the retired ones, which have the write-ups posted.
These are all staring point machines which have the write-ups published on the site.
The following two machines are active and have no write-ups available. The machines were rooted completely, I achieved both user and system access.